
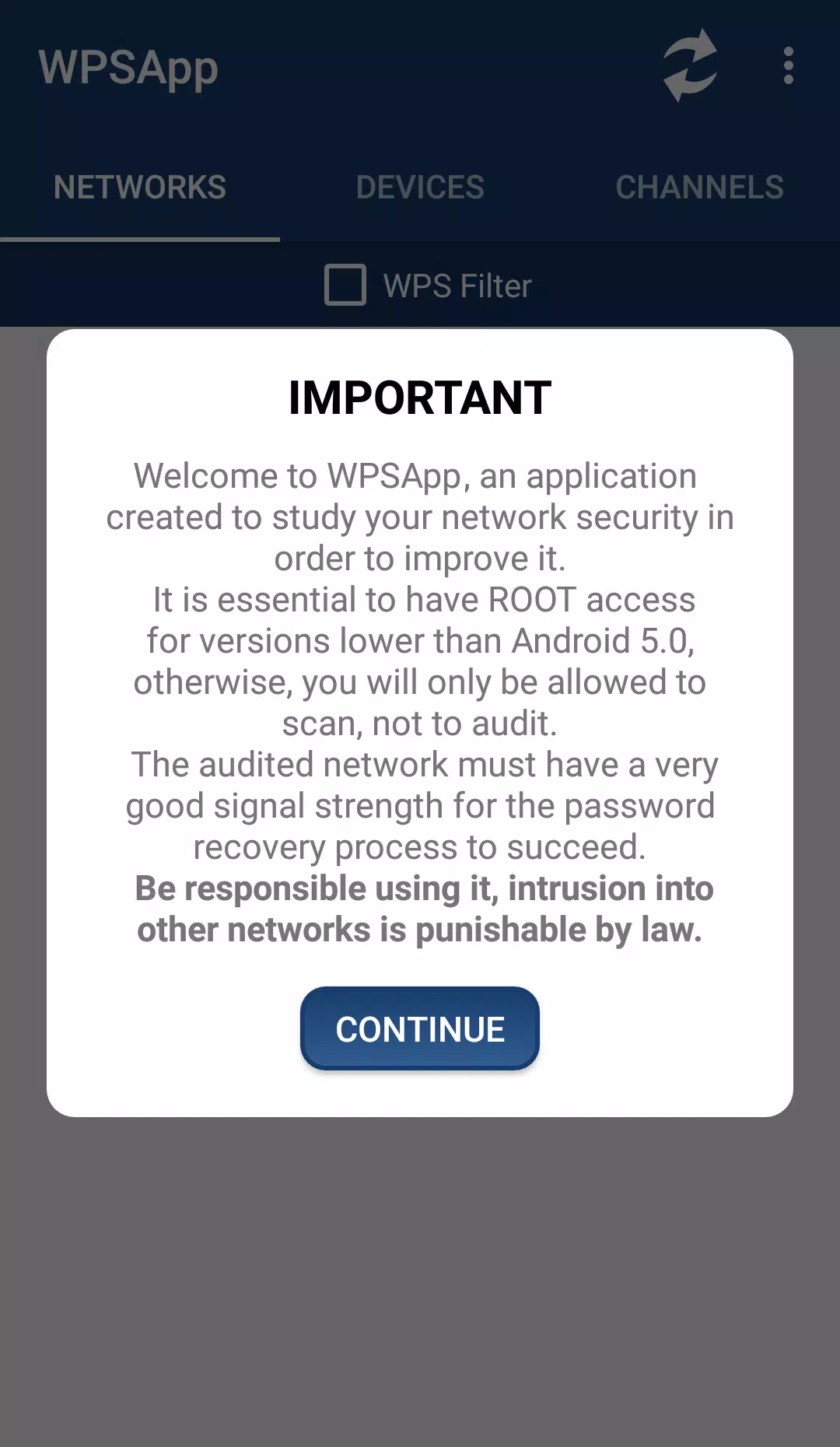
Application Description
Ever wondered if your WiFi network is as secure as Fort Knox or more like a sieve? Let's delve into the world of WPS protocol to find out. WPSApp is your trusty sidekick in this digital security adventure, designed to scrutinize your network's defenses by exploiting the WPS protocol. This protocol, meant to simplify WiFi connections with an 8-digit pin, can sometimes be a double-edged sword. Many routers from different manufacturers have pins that are either widely known or can be calculated, making them potential weak spots.
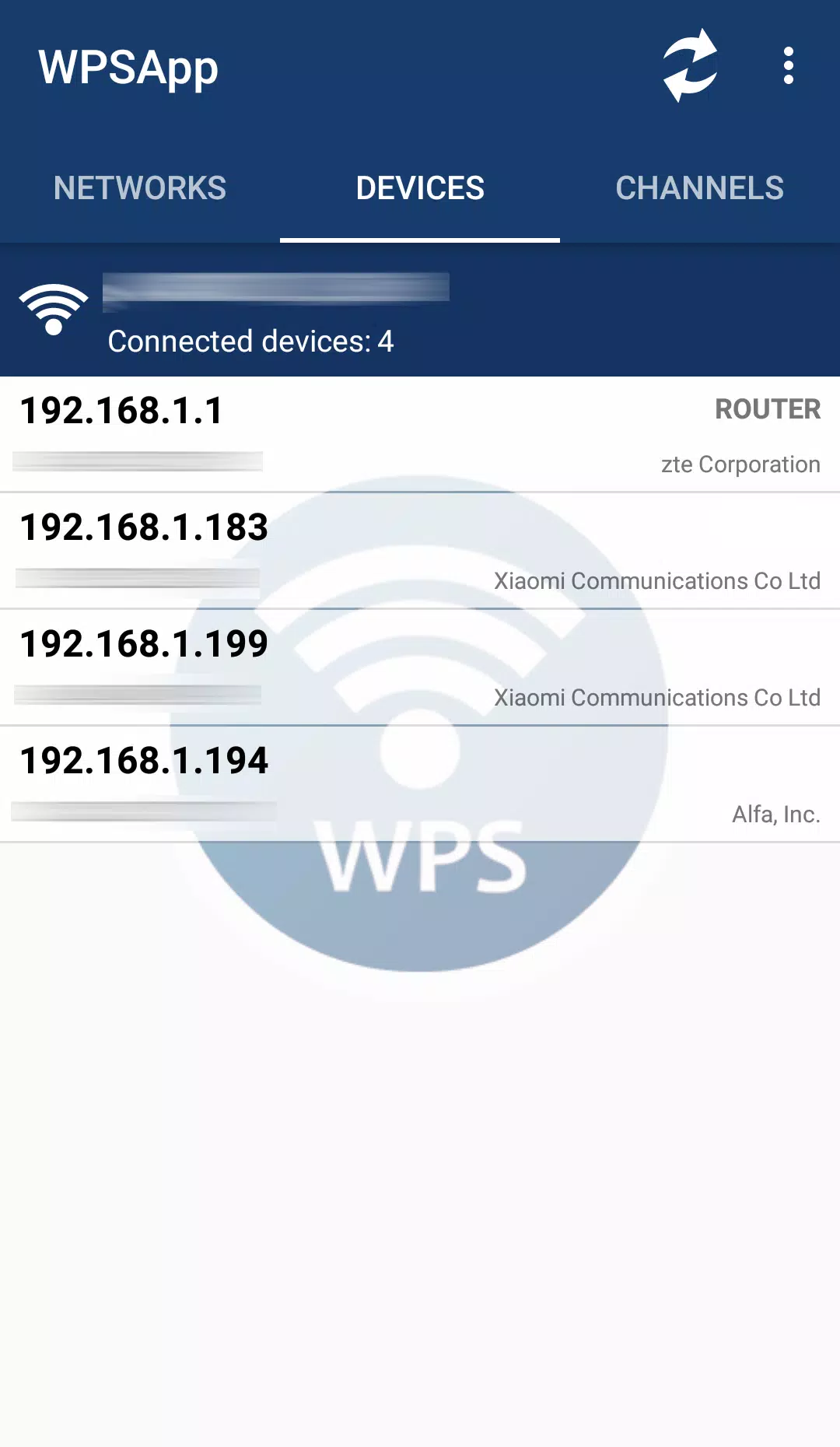
WPSApp harnesses these known pins to test your network's vulnerability. It employs various algorithms for generating pins and includes some default ones. Beyond just checking for WPS vulnerabilities, this app can also calculate default keys for certain routers, reveal WiFi passwords stored on your device, scan connected devices, and analyze WiFi channel quality.
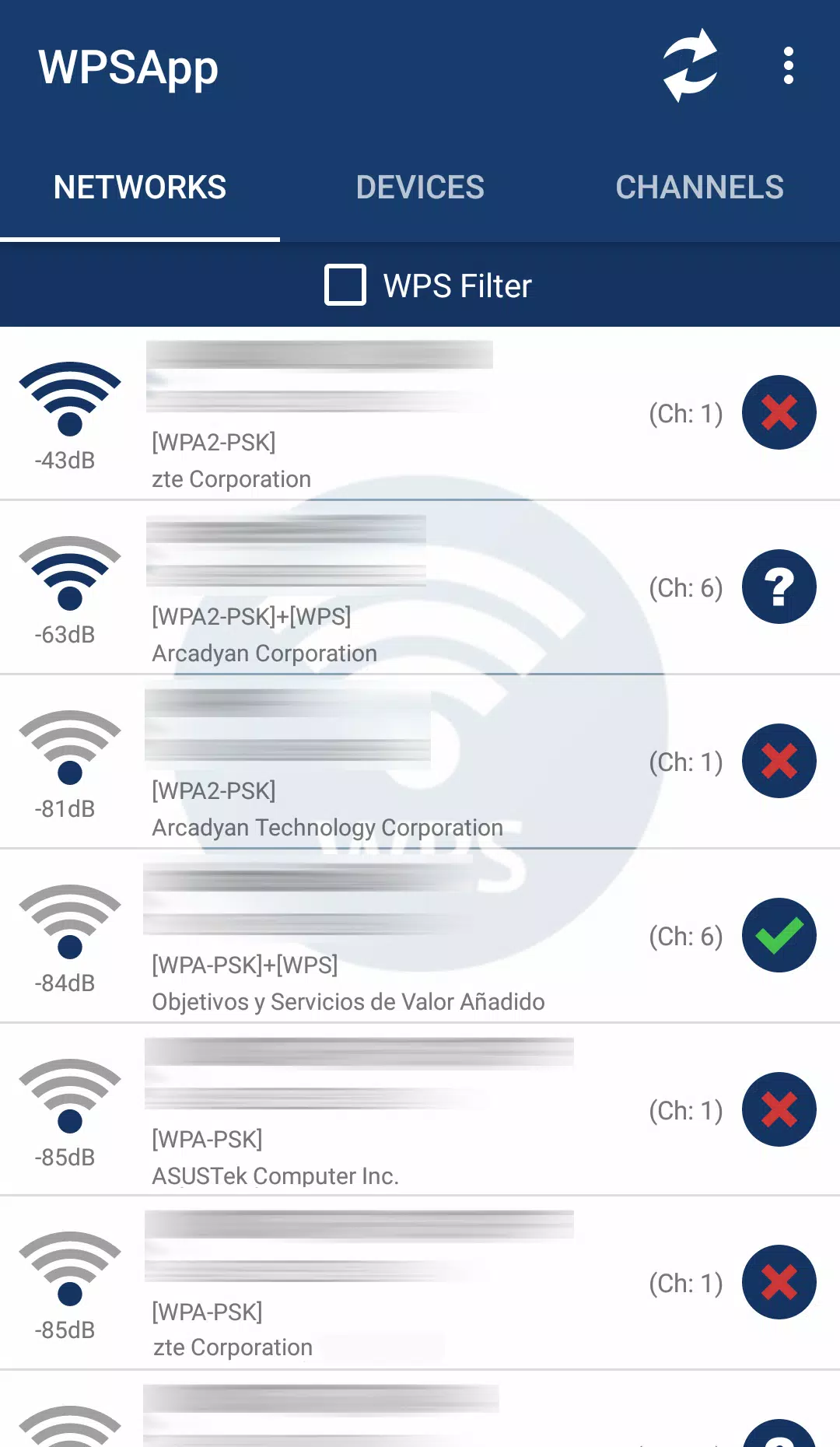
Using WPSApp is a breeze. When you scan nearby networks, you'll encounter three types of results:
- Networks marked with a red cross are considered "secure." These have the WPS protocol disabled, and their default passwords are unknown.
- Networks with a question mark have WPS enabled, but their pins remain a mystery. Here, the app lets you try the most common pins.
- Networks sporting a green tick are likely vulnerable. They have WPS enabled, and the connection pin is known. Alternatively, if the router has WPS disabled but the password is known, it will also appear in green, indicating you can connect using the key.
To fully leverage WPSApp, you'll need to be a Root user. This grants access to see passwords, connect on Android 9/10, and unlock some additional features.
Keep in mind, not all networks are vulnerable, and even if WPSApp flags one as such, it's not a guaranteed breach. Many router manufacturers have patched these vulnerabilities with firmware updates.
So, what should you do if your network is vulnerable? Simple: disable WPS and set a strong, personalized password. Remember, unauthorized network intrusion is illegal, so use this tool responsibly.
From Android 6 (Marshmallow) onwards, you'll need to grant location permissions due to new Google requirements. For more details, check out Google's documentation.
Note that some Samsung models encrypt passwords, displaying them as long hexadecimal strings. You might need to do some online research or contact the developer for decryption methods. Also, LG models with Android 7 (Nougat) have issues with pin connections due to their proprietary software.
Before you rate the app, take a moment to understand how it works. And if you have any suggestions, bug reports, or comments, feel free to reach out at [email protected]. Thanks to all the contributors who've made this tool possible: Zhao Chunsheng, Stefan Viehböck, Justin Oberdorf, Kcdtv, Patcher, Coeman76, Craig, Wifi-Libre, Lampiweb, David Jenne, Alessandro Arias, Sinan Soytürk, Ehab HoOoba, drygdryg, Daniel Mota de Aguiar Rodrigues.
Tools




 Application Description
Application Description  Apps like WPSApp
Apps like WPSApp 
















